Download the NIST SP 800-53 Checklist
Access our free PDF with all 12 essential steps to achieving compliance and ATO.

By submitting this form, you consent to TestPros, Inc. storing and processing your information to provide the requested content and communications. Privacy Policy
NIST SP 800-53 is a critical framework that establishes comprehensive security controls for federal information systems. These systems often handle highly sensitive data, making them prime targets for cyber threats. To protect national security, federal agencies must comply with NIST SP 800-53, which lays out clear standards for safeguarding information and mitigating risks.
Maintaining compliance with NIST SP 800-53 has become more important than ever as cyber threats evolve. Federal agencies face increasing pressure to implement robust security measures that not only protect their systems but also ensure the integrity of national security operations.
This is where TestPros comes in. As a trusted independent auditor, we help companies develop their ATO (Authority to Operate) packages, ensuring that both new applications and ATO renewals meet government requirements. With decades of experience, TestPros supports organizations in navigating the complexities of the NIST SP 800-53 framework, ensuring their ATO packages are accepted by their government customers.
What is NIST SP 800-53?
The NIST SP 800-53 framework was developed by the National Institute of Standards and Technology (NIST) to provide federal agencies with clear, actionable security standards. Its purpose is to ensure that federal information systems, which often contain sensitive and mission-critical data, are properly safeguarded against a wide range of cybersecurity threats.
The origins of NIST SP 800-53 trace back to the Federal Information Security Management Act (FISMA), which was enacted to improve the security of federal information systems. FISMA mandates that federal agencies implement NIST’s guidelines, making compliance with NIST SP 800-53 essential for protecting national security.
By establishing specific controls across areas like access management, system monitoring, and incident response, the framework helps agencies minimize risks.
At TestPros, we bring years of experience in guiding organizations through the complexities of NIST 800-53 compliance. We understand the detailed requirements that federal agencies demand and work closely with our clients to ensure their systems meet these standards.
Whether it’s developing a first-time ATO package or renewing an existing ATO, TestPros ensures that your organization adheres to NIST’s guidelines and satisfies government expectations, positioning you for success in your compliance efforts.
Why Compliance is Important
Compliance with NIST SP 800-53 isn’t just about security—it’s a requirement to secure your Authority to Operate (ATO). Without an active ATO, your content, application, or website cannot stay live. If your ATO expires or isn’t renewed, you must take everything down until compliance is reestablished.
For government contractors, this means your contract is tied directly to maintaining an active ATO. Websites, applications, or systems that serve federal agencies must comply with NIST 800-53 to keep operations running. In essence, no ATO means no website, no storefront, no system, and no contract.
How the ATO Process Works
The ATO decision hinges on an independent assessment report submitted directly to the government authority. After reviewing the report, the authority decides whether the identified risks are acceptable and determines whether to grant, conditionally approve, or deny the ATO.
TestPros delivers the independent assessment reports you need to obtain and maintain your ATO. Our team ensures that your compliance efforts align with federal standards so you can keep your systems live, protect your contracts, and avoid downtime.
Compliance doesn’t stop once you get your ATO—it’s an ongoing process. Vulnerabilities within supply chains or third-party vendors can jeopardize your status, so it’s essential to monitor and maintain compliance continuously. With TestPros by your side, you’ll be ready to meet challenges head-on, ensuring your systems stay operational and compliant.
NIST SP 800-53 Compliance Checklist
Achieving compliance with NIST 800-53 requires a structured approach. This framework is comprehensive, but following the right steps can ensure your organization is fully prepared to meet federal requirements. Let’s break it down.
Step 1: Perform System Categorization
System categorization helps determine the potential impact of a security breach (low, moderate, or high) on confidentiality, integrity, and availability. This is done according to FIPS 199 and NIST SP 800-60.
- Low Impact: Loss would have a limited adverse effect on organizational operations, assets, or individuals.
- Moderate Impact: Loss would have a serious adverse effect.
- High Impact: Loss would have a severe or catastrophic adverse effect.
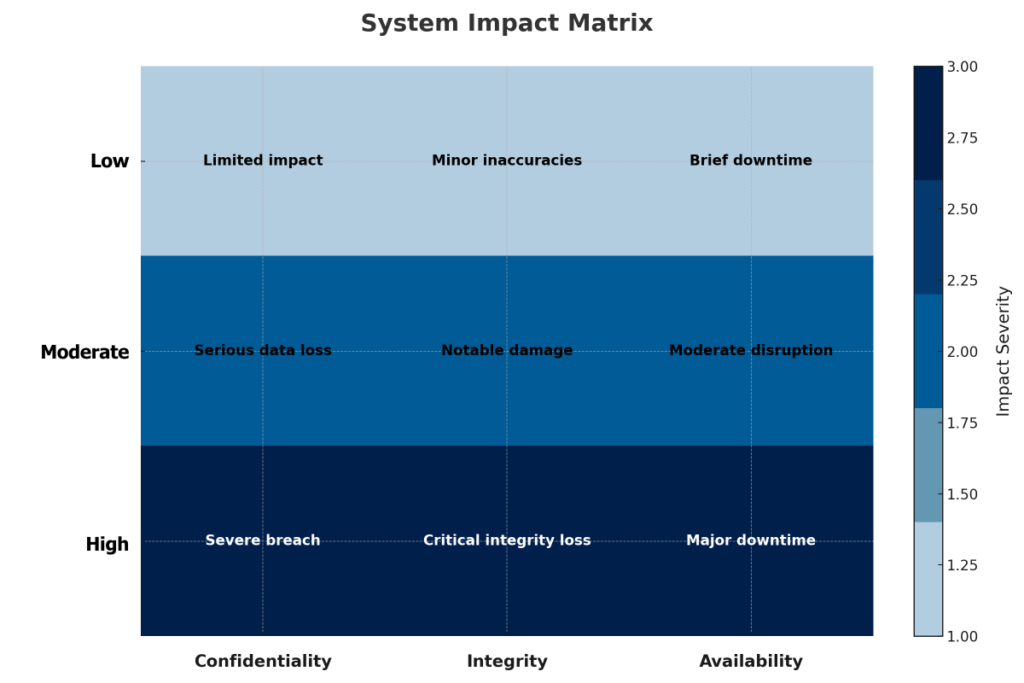
Categorizing the system establishes the baseline security requirements. It allows you to tailor the security controls to the system’s sensitivity and risk level. Without system categorization, you wouldn’t know which controls or the extent of protections are needed.
Categorizing the system first ensures that the appropriate scope of security measures is established, which can then be evaluated in more depth through the risk assessment.
Step 2: Perform a Risk Assessment
After categorizing your system, the next step is to conduct a risk assessment to identify specific threats, vulnerabilities, and risks associated with your systems. This assessment fine-tunes the selection and implementation of controls based on the actual risks your organization faces.
The risk assessment informs how rigorously the selected controls from the system categorization must be applied and monitored. It allows you to understand where your organization is most vulnerable, whether through internal processes, external threats, or third-party vendors.
During this process, it’s important to identify critical assets needing protection, such as sensitive data, communication systems, and other information systems vital to your operations. For federal systems, protecting these assets is crucial because they often directly relate to national security.
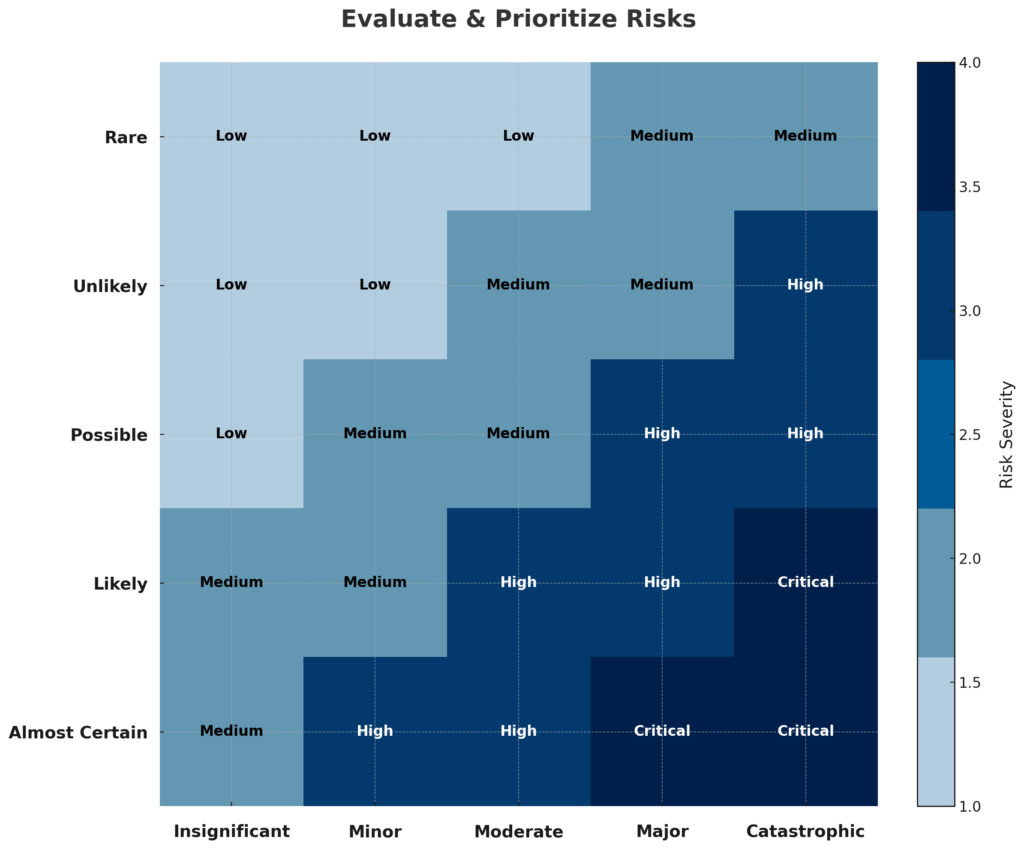
A comprehensive risk assessment should consider a broad range of potential threats—unauthorized access, data breaches, system failures, and insider threats, among others. By evaluating every possible entry point, you can prioritize risks based on their potential impact and likelihood of occurrence.
By addressing these vulnerabilities early, your organization can mitigate risks before they become significant issues. Ultimately, a well-executed risk assessment becomes the foundation of your NIST 800-53 compliance efforts.
Step 3: Identify Applicable Security Controls
Once your risk assessment is complete, the next step is to identify the specific security controls that apply to your organization. NIST 800-53 outlines 20 control families designed to address various aspects of security, from access control to system maintenance. These controls are a roadmap for implementing the necessary protections across your federal information systems. However, not all controls apply universally—some are more relevant depending on your organization’s structure, the type of data you handle, and the systems in place.
Here’s a list of the 20 control families:
- Access Control (AC) – Ensures only authorized users can access information systems.
- Awareness and Training (AT) – Focuses on educating personnel about security responsibilities.
- Audit and Accountability (AU) – Requires logging and tracking system activity.
- Security Assessment and Authorization (CA) – Involves the continuous monitoring of security controls.
- Configuration Management (CM) – Ensures systems are properly configured and maintained.
- Contingency Planning (CP) – Prepares for system disruptions or disasters.
- Identification and Authentication (IA) – Requires proper identification of users and devices.
- Incident Response (IR) – Ensures there is a clear process for responding to security incidents.
- Maintenance (MA) – Outlines policies for system maintenance and updates.
- Media Protection (MP) – Governs the handling and disposal of sensitive media.
- Physical and Environmental Protection (PE) – Secures physical access to systems and data.
- Planning (PL) – Requires strategic planning around system security.
- Program Management (PM) – Manages information security programs.
- Personnel Security (PS) – Focuses on screening and managing personnel with access to systems.
- Personally Identifiable Information Processing and Transparency (PT) – Focuses on the privacy of personal information within systems.
- Risk Assessment (RA) – Continually assesses risks and vulnerabilities.
- System and Services Acquisition (SA) – Ensures secure procurement of systems and services.
- System and Communications Protection (SC) – Protects system communications from unauthorized access.
- System and Information Integrity (SI) – Ensures systems and data remain accurate and secure.
- Supply Chain Risk Management (SR) – Addresses risks from external vendors and suppliers.
Now, how do you determine which control families apply to your federal information systems? Start by looking at the results of your risk assessment. The type of data you handle—whether it’s classified, controlled unclassified information (CUI), or general federal data—will directly impact which controls are essential.
For instance, if your systems manage highly sensitive information, you’ll need to focus heavily on Access Control (AC), System and Communications Protection (SC), and System and Information Integrity (SI).
Additionally, organizational structure plays a role. If your organization relies heavily on third-party vendors, Supply Chain Risk Management (SR) and System and Services Acquisition (SA) will be critical. Similarly, organizations with remote or field-based personnel will need to ensure their Identification and Authentication (IA) and Personnel Security (PS) controls are strong.
Every organization is different, and it’s important to map the controls to your specific operational needs and risks. Working through this step ensures that your security framework is tailored to the real-world challenges your organization faces in protecting federal information.
Step 4: Develop a System Security Plan (SSP)
Once you’ve completed the risk assessment, the next step is to develop a System Security Plan (SSP). The SSP is a key document that outlines how the selected security controls will be implemented, maintained, and monitored. It serves as a detailed roadmap for achieving and maintaining compliance.
The SSP includes critical information about the system, such as its purpose, environment, and security requirements. It should clearly describe each control and how it will address the identified risks. This documentation becomes essential during audits and ongoing reviews, as it demonstrates your organization’s commitment to securing sensitive information.
Developing an SSP early in the process ensures that you have a well-defined security strategy that can guide implementation and monitoring activities. By having a structured plan in place, you streamline communication and accountability across the organization.
For further reading on creating a comprehensive SSP, you may want to explore NIST SP 800-18, which guides security planning.
Step 5: Define Roles and Responsibilities
Assigning clear accountability helps prevent gaps in compliance and ensures that everyone understands their duties.
Key roles include the Information System Owner (ISO), responsible for the overall security of the system; the Information System Security Officer (ISSO), tasked with daily security operations; and the Authorizing Official (AO), who makes the final decision on whether the system is authorized to operate.
By clearly defining these roles, you establish a structure for security oversight and risk management. This not only facilitates smoother communication but also enhances the efficiency of the entire compliance process.
For more detailed insights on role definitions, you can refer to NIST SP 800-37, which discusses the Risk Management Framework (RMF) and the responsibilities of key personnel in the context of system security.
Step 6: Implement Security Controls
Once you’ve identified the relevant security controls for your organization, it’s time to put them into action. Implementing security controls involves a combination of technical measures and procedural processes that ensure your systems are protected on multiple fronts. These controls must address both the internal operations of your organization and the external risks posed by third-party vendors and supply chains.
Technical Controls
Technical controls are the tools and systems designed to prevent unauthorized access, detect anomalies, and safeguard sensitive data. Here are some common technical controls you should prioritize:
- Encryption: Encrypting data, both at rest and in transit, ensures that even if sensitive information is intercepted, it remains unreadable to unauthorized parties. This is critical for protecting classified or controlled unclassified information (CUI).
- Firewalls: A robust firewall setup creates a secure perimeter around your network, filtering incoming and outgoing traffic to prevent malicious access.
- Access Control Measures: Implement role-based access control (RBAC) or multi-factor authentication (MFA) to limit access to sensitive systems and data only to those who need it. This reduces the likelihood of internal threats and limits damage in case of a breach.
- Intrusion Detection Systems (IDS): An IDS monitors your systems for suspicious activities, alerting your team to potential threats as they occur, allowing for a fast response.
Procedural Controls
Procedural controls are the policies and processes that ensure your organization consistently maintains high-security standards. These controls involve educating your staff, creating clear policies, and establishing procedures for managing security incidents. Here are key procedural controls to focus on:
- Staff Training: Regular cybersecurity training is essential for ensuring that all employees understand their roles in maintaining security. This should include training on how to recognize phishing attacks, handle sensitive data, and respond to security incidents.
- Policy Creation: Develop and enforce clear security policies, including data handling protocols, incident response plans, and guidelines for system access. These policies should be communicated regularly and updated as threats evolve.
- Incident Response Plans: Having a documented and practiced incident response plan is crucial. This ensures your organization can quickly respond to and mitigate any security breaches or cyberattacks, minimizing damage.
Supply Chain Risk Management
One of the most overlooked aspects of cybersecurity is ensuring that your partners and vendors meet the same security standards. This is where Supply Chain Risk Management (SR) comes into play. Any weaknesses in your vendors’ security practices can expose your organization to significant risks.
To manage these risks effectively:
- Vendor Assessments: Conduct thorough assessments of your third-party vendors to ensure they comply with NIST 800-53 standards. This includes reviewing their security policies, procedures, and incident response capabilities.
- Contractual Security Clauses: Include security requirements in contracts with vendors to ensure they adhere to your organization’s security protocols.
- Ongoing Monitoring: Regularly review and monitor vendor performance, especially those who handle sensitive data or have access to critical systems.
Step 7: Document and Maintain Artifacts
After security controls are implemented, the next step is to maintain proper documentation. You must have a comprehensive record that proves your organization has taken the necessary steps to secure its systems. These records—known as artifacts—are the evidence you’ll need when it’s time for an audit or compliance review. Without them, your efforts could fall short.
So, what needs to be documented?
- Policies and Procedures: Your security policies, access control protocols, and incident response plans should all be thoroughly documented. These show how your security measures are enforced across the organization.
- System Configurations: Keep records of how your systems are configured—everything from network architecture to firewall rules and encryption protocols. This provides a technical blueprint of your security environment.
- System Logs: Logs capture real-time data on system activities like user access, configuration changes, and security events. These logs are your audit trail, helping to investigate and resolve any security incidents.
- Training Materials: Document your employee training efforts, including attendance and course content. This ensures your staff is up-to-date on how to handle sensitive data and respond to potential threats.
How Automation Tools Help
Automation tools can simplify the management of your documentation. They can automatically track system activity, flag missing artifacts, and ensure your records stay up to date. These tools take a lot of the manual work out of the process, making it easier to stay organized.
But here’s the important part: automation isn’t enough. While automation can help manage the volume of documentation, human oversight is still required. Someone must review the automated data to ensure it’s accurate and aligned with NIST 800-53 standards. There’s also no substitute for an independent review. Regular internal audits, coupled with independent validation from a trusted auditor like TestPros, ensure that your documentation is complete and meets federal requirements.
In short, combining automation with regular human oversight creates a system that’s both efficient and reliable. By keeping your artifacts well-documented and up to date, you’ll be well-prepared for any audit or compliance review. More importantly, you’ll ensure your organization remains secure and fully compliant with NIST 800-53 standards.
Step 8: Conduct Security Assessments and Penetration Testing
After implementing security controls, the next step is to conduct independent security assessments to verify the effectiveness of the applicable NIST 800-53 security controls.
Under NIST 800-53 Revision 5, independent penetration testing is strongly recommended at least every three years. These tests simulate real-world attacks to identify weaknesses that could be exploited by malicious actors. Regular penetration testing ensures that systems remain resilient as new threats emerge and security environments evolve.
Penetration testing results are sometimes required in the ATO package needed to meet compliance requirements. By demonstrating that the system has been tested for security vulnerabilities, the organization assures the Authorizing Official that risks have been evaluated and are being managed appropriately.
Step 9: Develop a Plan of Action and Milestones (POA&M)
Following the security assessments and penetration testing, the next step is to develop a Plan of Action and Milestones (POA&M). The POA&M outlines the steps that need to be taken to address any identified vulnerabilities or deficiencies.
In this document, each weakness is prioritized based on its severity and potential impact. The POA&M should also include deadlines for resolving the issues and assign specific individuals or teams responsible for the corrective actions. It ensures that there’s a structured plan to remediate risks, helping the organization stay on track toward full compliance.
The POA&M is often a critical part of the ATO package. The plan demonstrates that the organization is aware of any risks that remain and has a plan in place to mitigate them. This transparency is crucial when seeking approval from the Authorizing Official.
By creating a detailed POA&M, you provide a clear path forward to address vulnerabilities, maintain security, and comply with NIST 800-53 standards.
Step 10: Independent Audit and SAR
After developing the POA&M, the next step is to conduct an independent audit. This audit offers an objective, third-party review of the system’s security posture, ensuring compliance with NIST 800-53 requirements.
The independent auditor evaluates the implemented security controls, the results of the internal security assessments and penetration testing, as well as the POA&M. The audit verifies that the controls are functioning as intended and that any identified risks are appropriately documented and prioritized in the POA&M for remediation.
A critical outcome of the independent audit is the creation of the Security Assessment Report (SAR). This report consolidates the findings from the audit, including details on vulnerabilities, weaknesses, and the overall effectiveness of the security controls. The SAR is a key component of the Authorization to Operate (ATO) package, as it demonstrates that a comprehensive and impartial review has been conducted.
Once completed, the SAR is submitted to the government customer for review. The customer uses this report to make a decision on whether to grant or renew the ATO. The SAR is essential for both first-time ATOs (for new systems) and renewals for existing systems.
Ultimately, the SAR is what the Authorizing Official relies on to approve the ATO, making it one of the most crucial steps in achieving and maintaining NIST 800-53 compliance.
Step 11: Obtain Authorization to Operate (ATO)
It’s finally time for the ATO submission. The ATO is a formal decision made by the Authorizing Official (AO) that grants approval for the system to operate, based on its assessed security posture and risk management strategies.
The SAR plays a central role in this decision, providing the AO with a detailed evaluation of the system’s security, including any vulnerabilities, the effectiveness of the implemented controls, and the mitigation actions outlined in the Plan of Action and Milestones (POA&M). In addition to the SAR and POA&M, certain agencies also require penetration testing results as part of the ATO package.
At this stage, the AO will review the following:
- Security Assessment Report (SAR): Summarizing the independent audit and any security weaknesses or residual risks.
- Plan of Action and Milestones (POA&M): Detailing how and when remaining vulnerabilities will be addressed.
- Penetration Testing Report: (Where required) Ensuring that the system has been tested against potential exploitation methods and is adequately protected.
- Overall Risk Posture: Determining whether the system’s residual risks are acceptable and whether mitigation plans are sufficient.
Based on this review, the AO can make one of the following decisions:
- Grant the ATO: Allowing the system to operate with the acknowledged risks and mitigation strategies.
- Grant a Conditional ATO: Allowing operation but with specific conditions that must be met within a designated timeframe (often tied to the POA&M).
- Deny the ATO: If the system’s risks are too high and the remediation plans are insufficient.
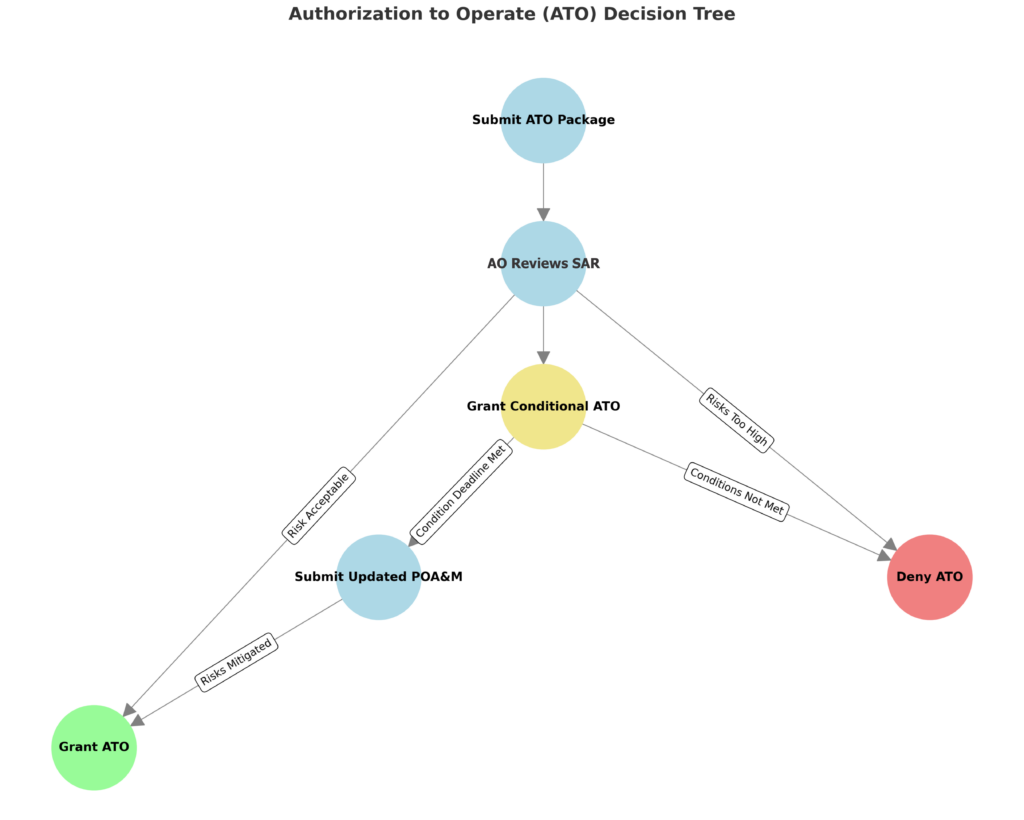
Achieving the ATO is necessary for both new systems and existing systems seeking to renew their authorization. Without it, the system cannot legally operate in its intended environment, particularly for federal agencies or government contracts.
Step 12: Continuous Monitoring
The final, and arguably the most crucial, step in maintaining NIST 800-53 compliance is continuous monitoring. This step is essential to ensuring your system remains secure and compliant long after the ATO is granted. It involves using automated and manual monitoring tools to detect vulnerabilities, performing regular vulnerability scans and penetration testing, and maintaining an effective incident response plan.
Continuous monitoring also includes updating security controls as needed, keeping the POA&M current, and conducting periodic risk assessments and compliance audits.
By proactively managing risks and regularly reassessing your system, continuous monitoring ensures ongoing compliance and strengthens your overall security posture.
Staying Compliant Beyond the Checklist
Following these 12 steps ensures that your organization has implemented the necessary controls, documented its efforts, and demonstrated compliance through independent audits and assessments. However, the final and equally important step is continuous monitoring. Threats evolve, systems change, and new vulnerabilities emerge. Regular monitoring ensures your organization stays ahead of potential risks and remains compliant over time.
TestPros can support you throughout this entire process. From helping you categorize your systems and develop a solid security plan, to conducting independent audits and assisting with your ATO submission, our experts ensure that every aspect of your NIST 800-53 journey is covered. Whether you’re preparing for your first ATO or renewing an existing one, we’ll help you meet federal requirements with confidence.
Ready to get started? Contact TestPros to ensure your organization is fully prepared for NIST 800-53 compliance—and keep your federal systems secure for the long term.





