
Getting Started
Cybersecurity compliance is a non-negotiable when working within the federal government. With cyberattacks growing more frequent, ensuring the protection of sensitive information is a top priority, especially those dealing with Controlled Unclassified Information (CUI). Any organization that has involvement with government contracts is required to meet strict security standards and properly safeguard valuable data at all times. Those that fail to comply can put national security at risk, as well as potentially jeopardize continued partnership with the government. Both NIST and Cybersecurity Maturity Model Certification (CMMC) can assist with maintaining a healthy cybersecurity posture.
This article will discuss CMMC and NIST SP 800-171 more in-depth, outline the key differences between the two programs, provide some unexpected benefits that come with CMMC, understand the current partnership between CMMC and NIST SP 800-171 revision 2, and finally, explore the next steps contractors can take to understand which path best suits their organization.
Understanding CMMC

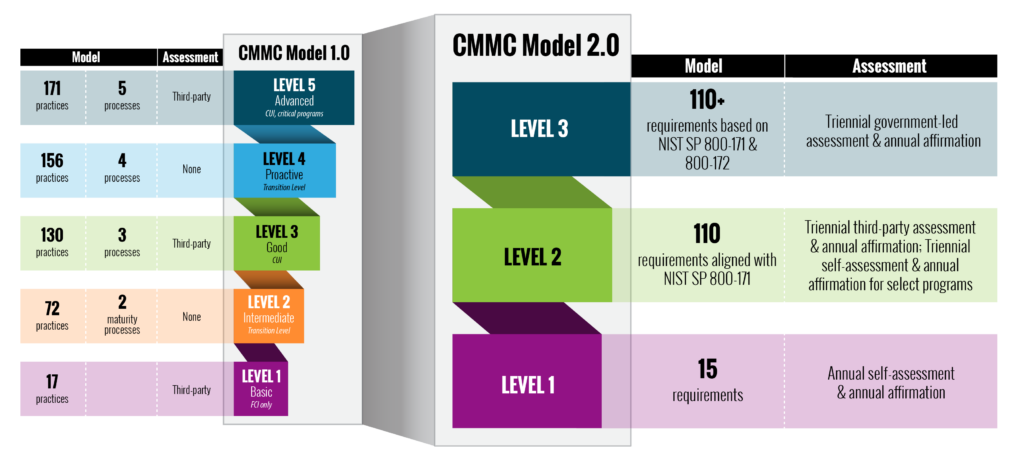
CMMC, specifically model 2.0, is comprised of three different tier maturity levels that build upon one another to ultimately provide a streamlined approach to cybersecurity compliance. It is utilized as an auditing process and allows organizations to get an in-depth look at the current cybersecurity posture- ensuring all required security controls and minimum standards are being met.
CMMC represents a shift towards trying to simplify and clarify potentially confusing IT cybersecurity requirements for defense contractors. In previous years, CMMC had framework model 1.0, the shift to 2.0 has removed unnecessary complexities making it easier to implement. The reduction of controls and excess requirements has allowed organizations to create a main focus on impactful cybersecurity practices, rather than being overwhelmed by a plethora of items that may not have applied. The reduction truly allows for flexibility within the path of compliance.
Another key element is the certification process itself. The different tier levels within the new framework allow for organizations handling less sensitive data- to perform self-assessments, with the potential for government or third-party audits at a later date. This specific approach strikes a balance between ensuring strong security practices while avoiding the monetary cost and burden on a smaller contracting team. This process allows for contractors to maintain certification over time, and have a solid understanding of the current cyber health posture at any given time.
Understanding NIST SP 800-171

NIST SP 800-171 is a highly respected set of standards and guidelines that organizations working with the Department of Defense (DoD) must adhere to. It is a contractual requirement for any contractor, vendor, or supplier that processes, stores, transmits, or protects CUI. Cybercrime within different areas of the supply chain has been a primary target over the years. The cybersecurity guidelines from NIST publications are a way to help combat it. The controls outlined in NIST SP 800-171 are in place to ensure organizations are following the industry’s best practices to secure sensitive data in order to meet defense industry expectations.
In May of 2024, the National Institute of Standards and Technology (NIST) published NIST SP 800-171 revision 3. The purpose of the update was to create more defined parameters and withdraw controls that were no longer considered impactful. Although controls were withdrawn, the addition of more families had been implemented. This change was to maintain alignment with other publications NIST released, such as NIST SP 800-53B.
Key Differences Between CMMC Compliance and NIST SP 800-171
While both NIST SP 800-171 and CMMC do have similar goals, such as the protection of Information Systems, they do offer two very different paths and requirements. Depending on the organization’s needs and the monetary funds available, one may be more beneficial than the other.
Auditing vs Assessment
CMMC directly builds upon the standards set forth by SP 800-171, however, it goes a bit further by introducing the aspect of a certification requirement. During tier 2 and tier 3 of the CMMC model, there is a requirement to obtain a third-party assessment and validation. This would confirm that all security controls are being met. The validation process acts as an audit and must be conducted by an independent team with no ties to the organization. Tier 3 does specify government-led audits.
NIST on the other hand, although it offers all controls listed in SP 800-171 and is very detailed, it was designed for organizations to conduct self-assessments and monitor the cyber health posture in real-time. Organizations using this method can choose to create a Plan of Action and Milestones (POA&Ms) where needed if a self-audit reveals an area of weakness. The POA&M is a detailed description of the plan or process that will mitigate the risk at a later date.
CMMC Levels and Structure
As previously mentioned, CMMC 2.0 revolves around a three-tiered model. Level 1 is foundational, Level 2 is advanced, and Level 3 is expert. Each tier corresponds to the sensitivity of the data and adds various security practices that are required. Level 1 focuses on basic cyber hygiene practices, essential for contractors handling Federal Contract Information, while Level 2 builds on these controls and begins incorporating a large portion of NIST SP 800-171 controls that focus on CUI. Level 3 incorporates more advanced practices aligned with NIST SP 800-171 & SP 800-172. CMMC is all about offering flexibility where possible all while maintaining a solid cybersecurity health posture.
NIST SP 800-171 revision 3 is comprised of 17 control families, 3 more than what revision 2 had. Those organizations solely utilizing NIST as a compliance checklist are required to address all controls listed in each family and know which apply and should be implemented. Unfortunately, there is no formal structure available for organizations to verify compliance or if all controls have been met to the satisfaction of, say the DoD.
NIST SP 800-171 standards set the baseline for security, but CMMC builds upon it ensuring compliance is achieved and maintained throughout the lifecycle of the contract.
Scope and Applicability
NIST is a well-recognized set of standards. It is widely used across the U.S. Government, but more broadly across all contractors, not just DoD contractors. Due to this, the guidelines try to make it relevant to a wider audience.
CMMC is more specific to those working directly within the DoD. CMMC applies to all DoD contractors and subcontractors regardless of organizational size. The DoD focuses on the CMMC model as an effort to secure the defense industrial base (DIB) from growing cyber threats. DoD wants to ensure all members are equipped to protect the DoD assets, including IS and sensitive data.
Compliance Requirements
Within each level of the CMMC model there are different controls and security requirements that must be met. At Level 1, only 17 security practices need to be addressed, at Level 2, all 110 NIST SP 800-171 controls should be adhered to, and lastly, Level 3 requires all 800-171 controls plus additional security measures found in 800-172.
NIST SP 800-171 compliance is straightforward and only requires the controls listed within the publication to be addressed. SP 800-171 revision 3 has been released, however, CMMC 2.0 still requires SP 800-171 revision 2 to be followed. It takes time for new rules to be reviewed and implemented in a manner that benefits all parties. Throwing new requirements at organizations without properly understanding the ramifications it may cause could do more harm than good.
Impacts on Contractors
NIST and CMMC both will require additional resources, sometimes from a personnel standpoint, other times from a financial standpoint, and even possibly an asset standpoint. There is a lot of preparation that goes into CMMC and the whole certification process. The organization must also pay a team of auditors and agree to fix the controls that are not being met.
NIST, since it is a self-assessment, may have more of a lenient timeline, however, all controls should still be addressed in some form or fashion. Resources still will need to be allocated and personnel will need to understand the required cybersecurity practices to secure CUI or other sensitive data.
Benefits of CMMC
Holding a CMMC certification provides a significant advantage over organizations that only opt for NIST compliance. While NIST compliance is essential, as it is a comprehensive list for CUI, the CMMC certification provides a higher level of trust and credibility with the DoD and other federal agencies. Certified organizations demonstrate a proactive commitment to maintaining robust security measures, which can then lead to increased opportunities for future DoD contracts. The defense sector has mandated the CMMC model and has made it a minimum requirement for compliance purposes.
Those who follow the CMMC model also benefit from having that enhanced security posture. Organizations reduce their overall risk of cyberattacks and it helps ensure they are better equipped to protect sensitive information.
The community surrounding the CMMC model can be helpful as well. CMMC offers resources available for things such as incident reporting. The DoD wants organizations to succeed and be able to combat any cyber threats that may arise.
Partnership Between CMMC and NIST SP 800-171
CMMC without NIST is incomplete. NIST is the backbone of the CMMC model and allows the DoD to take a concept that works well and expand on it to make it more tailored to their needs. It’s a streamlined process that reinforces industry standards yet utilizes it in a way that can continuously evolve as new cyber threats emerge.
The US Government does incorporate various publications of NIST standards across a wide variety of organizations. By utilizing SP 800-171, it gave a seamless feel.
SPRS Scores
Supplier Performance Risk System (SPRS) scores play an important part for both CMMC and NIST SP 800-171 compliance. These scores range from -203 to +110, representing an organization’s cybersecurity posture. Contractors working with the Department of Defense must have a high SPRS score, as it directly impacts their ability to win contracts and maintain existing partnerships.
To achieve a top score, organizations must demonstrate full compliance with NIST SP 800-171 requirements and implement additional security measures. A higher score not only increases the chances of securing DoD contracts but also reflects a stronger overall cybersecurity stance, which is vital in today’s threat landscape.
Timeline for Compliance
Reaching full compliance with CMMC or NIST SP 800-171 doesn’t happen overnight. Organizations should expect to dedicate significant time and resources to achieve and maintain compliance. The timeline can vary greatly, typically ranging from 3-12 months or more, depending on the organization’s size, current security posture, and available resources.
This extended timeline accounts for various stages, including:
- Initial Assessment and Gap Analysis: 2-4 weeks
- Evaluate current security practices against required controls
- Identify areas needing improvement
- Development of Policies and Procedures: 1-3 months
- Create or update documentation to align with compliance requirements
- Establish new processes and workflows
- Implementation of Security Controls: 2-6 months
- Deploy necessary technical solutions
- Configure systems and networks to meet security requirements
- Train personnel on new procedures
- Internal Audits and Testing: 2-4 weeks
- Conduct thorough assessments of implemented controls
- Identify and address any remaining gaps
- SPRS Score Calculation and Improvement: 1-2 months
- Determine initial SPRS score
- Implement additional measures to improve score if needed
- Preparation for Third-Party Audits (CMMC specific): 1-2 months
- Gather and organize all required documentation
- Conduct mock audits to ensure readiness
- Third-Party Assessment (for CMMC certification): 2-4 weeks
- Schedule and undergo official CMMC assessment
- Continuous Monitoring and Maintenance: Ongoing
- Regularly review and update security practices
- Address new threats and vulnerabilities as they emerge
These timelines are approximate and can vary significantly based on individual circumstances. Some organizations may be able to complete the process more quickly, while others may require additional time to address complex security challenges or resource constraints.
Next Steps for Contractors

It’s imperative for an organization to first understand the scope of the CUI. Understanding boundaries and the details of the information present is key deciding as to which route of cybersecurity compliance is best. Here is a list of questions that can be asked to make a more informed decision.
- What is the current cybersecurity compliance status?
- What types of data get handled?
- What are future plans with government contracts?
- What internal resources are currently available?
- How confident is the team with the ability to self-assess compliance?
- How often are the cybersecurity practices audited/ updated?
- Is there a monetary constraint for implementing cybersecurity frameworks or best practices?
These questions should help begin an open dialog with the team and help make a more informed decision. The certified staff at TestPros offer various types of services to assist with CMMC and the compliance process if needed. Click to read more about FAQs and key benefits of CMMC.
Final Thoughts
The cyber world is unpredictable. Adversaries are exposing vulnerabilities left and right and penetrating systems to gain precious data. The US Government will always have a target on its back due to the sensitive information it holds. Supply chains, vendors, contractors, and all the third-party personnel in between are more likely to create a vulnerability. Incorporating different methods of security compliance can drastically increase the cyber health posture of any organization. Utilizing NIST SP 800-171 or the CMMC model are both great methods for those organizations looking to protect CUI.
Ready to take the next step in achieving federal cybersecurity compliance? Contact TestPros today for expert guidance on navigating your requirements. Our certified professionals are here to help you safeguard your data and secure your government contracts. Schedule your free consultation now!
References Utilized
- Cybersecurity Maturity Model Certification. Chief Information Officer > CMMC. (n.d.). https://dodcio.defense.gov/CMMC/
- DoD. (n.d.). Cybersecurity Maturity Model Certification (CMMC) proposed Rule Overview. Defense Visual Information Distribution Service. https://www.dvidshub.net/video/912871/cybersecurity-maturity-model-certification-cmmc-proposed-rule-overview
- Graham , D., Sawyer , J., Hummel, E., & Long, B. (2023, December 28). DOD rings in 2024 with proposed CMMC Rule. McDermott Will & Emery. https://www.mwe.com/insights/dod-rings-in-2024-with-proposed-cybersecurity-maturity-model-certification-rule/
- NIST releases final version of NIST SP 800-171, revision 3. Crowell. (2024, May 14). https://www.crowell.com/en/insights/client-alerts/nist-releases-final-version-of-nist-sp-800-171-revision-3
- Ross, R., Pillitteri, V., Dempsey, K., Riddle, M., & Guissanie, G. (2020, February). NIST Special Publication 800-171 Revision 2.
- Ross, R., Pillitteri, V. (2024, May). NIST Special Publication 800-171 Revision 3.




