Table of Contents
With attention on DFARS 252.204-701, the Cybersecurity Maturity Model Certification, and NIST SP 800-171, you may already be familiar with safeguarding requirements for Controlled Unclassified Information (CUI). However, are you aware of the requirements for safeguarding Federal Contract Information (FCI)?
You may be wondering – What is FCI? How is FCI different from CUI? Does it apply to my organization? What are the requirements for safeguarding FCI? How do I comply with FCI safeguarding requirements?
Answers to those questions and more will be answered! Here is what we will cover in this article:
What is Federal Contract Information (FCI)?
Generally speaking, if your organization handles information generated by or for the Government under a contract, it is highly likely you have FCI and must meet certain safeguarding requirements.
Federal Acquisition Regulation (FAR) 52.204-21 Basic Safeguarding of Covered Contractor Information Systems describes FCI as, “information, not intended for public release, that is provided by or generated for the Government under a contract to develop or deliver a product or service to the Government”.
In addition, FAR 52.204-21 applies to any information system used to collect, process, maintain, use, share, disseminate, or dispose of said information. Some of the systems within your own organization may include servers, user laptops and desktops, email systems (cloud based or otherwise), and more.
Lastly, it is important to note that FCI does not apply to information provided by the government to the public or transactional information (e.g., process payments).
FCI sounds similar to CUI, but how are they different?
How is FCI different from CUI?
While FCI more or less applies to all information produced by or for the Federal government, information designated as CUI is government information requiring additional safeguarding. What is CUI?
CUI is, “information the Government creates or possesses, or that an entity creates or possesses for or on behalf of the Government, that a law, regulation, or Government-wide policy requires or permits an agency to handle using safeguarding or dissemination controls.”
Sound similar to FCI? That is because while they are different, CUI is nearly always FCI, but FCI might not be considered CUI. What are some of the key differences between FCI and CUI?
- CUI is supposed to be specifically designated and marked as such
- Your contract should include a clause which indicates the potential for CUI to be handled during the performance of a contract, as well as the requirements for safeguarding said information
- CUI requires implementation of requirements found in NIST SP 800-171, while FCI requires implementation of controls found in FAR clause 52.204-21
- For organizations with DoD contracts, CMMC Level 1 security controls are inclusive of the safeguarding requirements and procedures for FCI
- CUI is mandated via Executive Order 13556 and implemented by the National Archives, while FCI is mandated via Federal Acquisition Regulations.
Still having difficulty understanding the difference between FCI and CUI? NARA provided the following useful chart that may help:
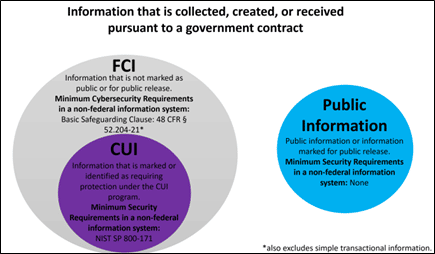
If FCI does not require consist of the same safeguarding requirements as CUI, what is required?
Safeguarding Requirements and Procedures for FCI
FCI requires, at a minimum, implementation of fifteen (15) safeguarding and handling requirements consistent with basic cyber hygiene. Those fifteen (15) requirements include:
- Limit access to systems which store, process, and/or transmit FCI. This applies to both users, processes acting on behalf of users (e.g., automated system processes), and devices (e.g., computers, printers, mobile devices, etc.). This is an important component to access control and may also be referred to role-based access control (RBAC). In short, maintain a list of users and devices that are authorized to access your system, what those users and devices are allowed to do on your system, and have a means for enforcing those policies.
- Only authorized users should have access to FCI and privileged (e.g., administrative) system access should be limited. In other words, a user should not have administrative privileges if they are not a system administrator and do not require said privileges.
- Connections to and use of information systems your organization does not control – or external systems – should be limited. This could be accomplished via content filtering, whitelisting and blacklisting of websites/systems users can access, or even just disallowing access to the public internet altogether.
- Ensure that FCI is not posted or processed on publicly available systems. Your organization should have a process in place to control the posting or processing of any information on publicly accessible information systems. That process should include review of information to ensure FCI was not intentionally or inadvertently included in said posting or processing.
- Have a means for authenticating users, processes, or devices as a prerequisite to allowing access to systems used for handling FCI. This may be accomplished through password protecting your organizational systems and/or establishing some other form of a trust-based relationship between users/devices and system (e.g., PKI authentication).
- Sanitize or destroy information system media containing Federal Contract Information before disposal or release for reuse.
- Have a mechanism for limiting physical access to systems with FCI (e.g., door locks).
- Escort visitors and monitor visitor activity
- Maintain audit logs of physical access to your facilities or areas of your facility with FCI
- Control and manage physical access devices, such as keys, codes to enter gates/doors, keyless entry cards, etc.
- Monitor, control, and protect organizational communications (i.e., information transmitted or received by organizational information systems) at the external boundaries and key internal boundaries of the information systems.
- Implement subnetworks for publicly accessible system components that are physically or logically separated from internal networks.
- Identify, report, and correct information and information system flaws in a timely manner.
- Employ the use of antivirus / antimalware on information systems.
- Ensure antivirus / antimalware software or hardware (for those with fancy next generation firewalls) are updated when new definitions or versions are available.
- Perform periodic scans of the information system and real-time scans of files from external sources as files are downloaded, opened, or executed.
Flow Down of Contractual Requirements
Lastly, one of the requirements in FAR clause 52.204-21 is to ensure your obligation to safeguard FCI is also an obligation for your subcontractors if they are also handling FCI. From the FAR:
The Contractor shall include the substance of this clause, including this paragraph (c), in subcontracts under this contract (including subcontracts for the acquisition of commercial items, other than commercially available off-the-shelf items), in which the subcontractor may have Federal contract information residing in or transiting through its information system.”
Conclusion
While this may seem like a lot, these requirements are not too difficult to implement and will better safeguard your organization’s information and operations, even if were not used to handle FCI.
If your organization needs some assistance with assessing your organizations current cybersecurity posture, organization is currently meeting these requirements, would like some help implementing cybersecurity controls or managing your network, or would even like help understanding these requirements further, contact us today!
References
[1] FAR 52.204-21