Table of Contents
In the world of cyber, things are constantly changing. Cyber tactics have evolved, technology has become increasingly sophisticated, and new vulnerabilities have emerged. National Institute of Standards and Technology, or NIST, has once again updated its publication that provides agencies with security requirements for protecting the confidentiality of Controlled Unclassified Information for nonfederal systems.
What is NIST SP 800-171 Revision 3?
Defense contractors and supply chains operating under Department of Defense (DoD) contracts are obligated to showcase a profound commitment to cybersecurity, prioritizing the protection of Controlled Unclassified Information (CUI). The DoD, being a prime target for advanced cyber threats, mandates stringent cybersecurity measures to safeguard sensitive data pertaining to national security and defense operations. Following the guidelines of NIST SP 800-171 has become a fundamental practice forcompliance with necessary cybersecurity protocols.
Initial Public Draft
Currently, NIST SP 800-171 Revision 3 has been released to the public as an Initial Public Draft (IPD) with plans to be updated to its final form by early 2024. The complexity of this document is not necessarily due to the controls itself, but rather the responsibility that NIST has to ensure the document meets all requirements of the Federal Information Security Modernization Act, Executive Order 13556, CUI Federal Regulation, and Office of Management and Budget (OMB) Circular A-130.
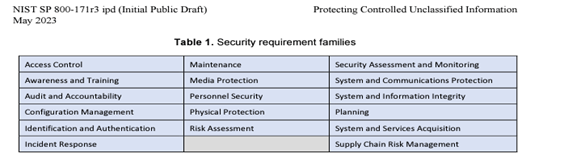
With the new iterations of the publication, it has slowly adopted the terminology and controls found in more rigorous NIST publications such as NIST SP 800-53. The authors have expanded the 800-171 publication to include 17 control families, all focusing on the confidentiality of CUI in nonfederal systems and organizations.
Primary Changes Between NIST SP 800-171 Revision 2 and Revision 3
In the updated revision, three new families- Planning, System and Service Acquisition, and Supply Chain Risk Management- have been integrated. These were all aspects that were absent in the previous revision. Other security measures that were deemed outdated or repetitive have been either refined or eliminated for improved efficacy.
Other changes included:
- Updated Security Requirements
- Clarification of Verbiage
- Reorganized to Align with NIST Cybersecurity Framework
- New Assessment Procedures
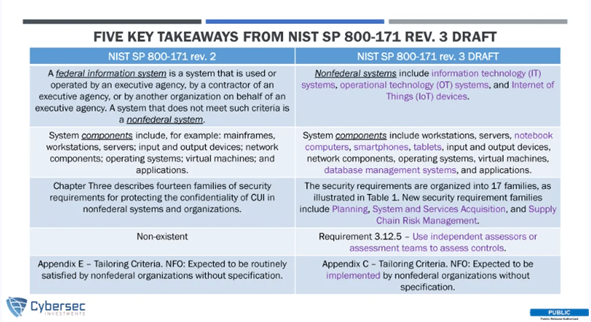
Cybersec Investments outlined the most noteworthy takeaways from the new Revision 3 Draft
How CMMC Comes into Play
CMMC or the Cybersecurity Maturity Model Certification, is essentially the auditing process completed by a third-party for the contractors, supply chain, and vendors working under a DoD contract. The CMMC auditing process provides an in-depth look at all the required security controls and determines if the organization is meeting minimum standards regarding cybersecurity, specifically focusing on CUI.
According to the Chief Information Officer of the U.S. Department of Defense, CMMC version 2.0 was established to ultimately protect sensitive national security information. The CIO hopes CMMC version 2.0 will simplify compliance standards for organizations by allowing for some portions of the CMMC to be a self-assessment and for other portions of the CMMC to have a heavier focus on DoD priorities. Ultimately, the goal is to achieve a partnership between the DoD and industry organizations, all while keeping evolving cyber threats at the forefront of conversations.
CMMC version 2.0 has three distinct levels- foundational, advanced, and expert.
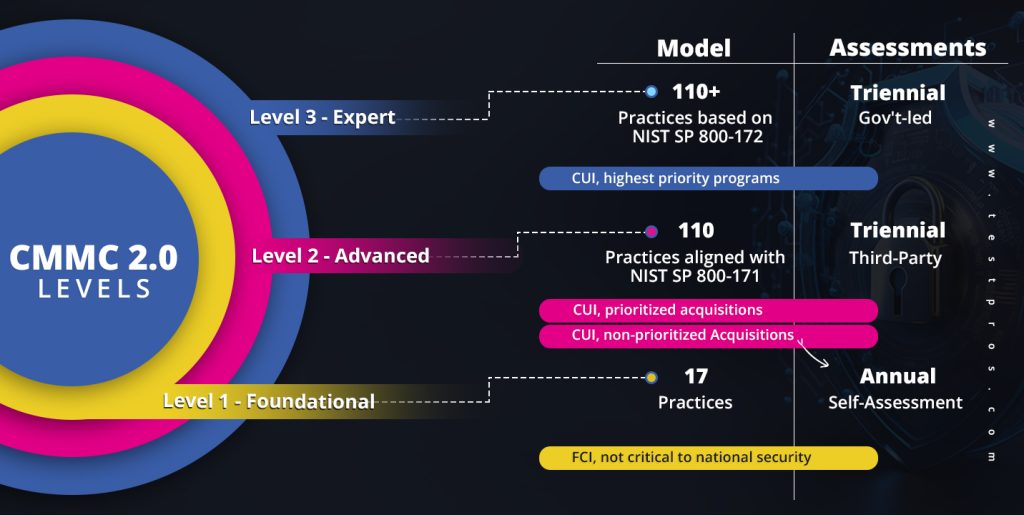
Each of these requires a different set of goals to meet to be compliant. Each tier builds on the next and the end goal is to have an assessment conducted triennially, meeting all expectations and security requirements put forth by DoD and NIST.
Download the CMMC 2.0 Checklist

Challenges Migrating to NIST SP 800-171 Revision 3
Given the complexity of this matter, it’s crucial for everyone involved to be in sync prior to making NIST SP 800-171 Revision 3 and CMMC compliance a mandatory standard. CMMC cannot fully update assessment guides and training material until NIST authors have released the official updated version. Subsequently, assessors will need to meet with the organizations and perform assessments. James Goepel, Co-Founder of CMMC Information Institute, believes that NIST SP 800-171 Revision 3 may likely not be enforceable until Q1 of 2025, giving everyone time to adapt to the new changes. The DoD Chief Information Officer will ultimately be the deciding factor as to when, or if, NIST SP 800-171 Revision 3 will even be utilized within the DoD.
Another challenge that both the DoD and NIST currently face is the rapid pace of cyber advancements and cybercrime tactics. Katie Arrington, a former Chief Information Security Officer at the DoD and a CMMC expert, shared her frustration and noted that once NIST SP 800-171 Revision 3 gets finalized, portions of it will already be outdated and obsolete.
What Can Organizations Do Right Now to Prepare?
Cybersecurity experts strongly recommend organizations to persist in their pursuit of CMMC compliance by aligning with the existing NIST SP 800-171 Revision 2 standards. It’s anticipated that the upcoming finalized Revision 3 will further evolve from the foundational concepts outlined in Revision 2. NIST’s guidance across all publications is expected to maintain a trajectory of increasing stringency, emphasizing stricter adherence over time rather than leniency. Upholding a robust security posture through compliance with the prevailing standards in Revision 2 and achieving CMMC certification under this assessment version offers two significant advantages for organizations.
- Organizations compliant with NIST 800-171 Revision 2 stand to benefit from a grandfathering provision. This affords organizations a gradual transition into Revision 3, promoting a more systematic approach rather than diving headfirst and potentially getting overwhelmed.
- Demonstrating adherence to essential policies and compliance standards is highly advantageous when vying for DoD contracts. The DoD seeks to collaborate with organizations displaying a strong cybersecurity orientation and a comprehensive grasp of effective methods to safeguard sensitive information. For the DoD, undertaking a contract without NIST validation poses a substantial risk, underscoring the importance of meeting established cybersecurity standards.
Organizations should remain proactive and not halt progress while awaiting final revisions. Sustaining a strong security posture acts as a deterrent against malicious actors, minimizing the risk of cybercrime and potential business disruptions. Every minute of network downtime can amount to approximately $5400 in losses, coupled with the added detriment of compromised reputation.
Final Thoughts
In the ever-evolving landscape of cybersecurity, adapting and staying ahead of the curve is crucial. NIST SP 800-171 Revision 3 represents a pivotal milestone, reflecting the industry’s dedication to enhancing security measures and effectively addressing cyber threats. As organizations wait for the finalized revision, understanding the nuances and aligning with the present NIST SP 800-171 Revision 2 can be a strategic advantage. NIST, coupled with the audits of CMMC, forms a solid defense and strengthens the organization’s cybersecurity health posture.