Unauthorized access and disclosure of government information has become all too common in these times of frequent cyber-attacks. As a result, the government has extended mandatory safeguards – found in NIST SP 800-171 – to non-federal organizations that process, store or transmit Controlled Unclassified Information (CUI) or Covered Defense Information (CDI) in non-federal information systems.
These non-federal organizations may include prime contractors, subcontractors, suppliers, distributors, and other service providers. Additionally, CUI is often provided to, or shared with, state and local governments, colleges and universities, and independent research organizations.
Do you need to make sure your organization complies with regulations?

What Does NIST SP 800-171 Compliance Require?
To comply with CUI safeguarding requirements, government contractors and other organizations processing CUI must fully understand what information they store, process, or transmit in the course of doing business with the federal government.
Defense industrial base contractors and suppliers must be prepared to provide adequate documentation describing their technical solutions, policies, and evidence of being able to detect and respond to incidents. safeguards, as defined by National Institute of Standards and Technology (NIST) Special Publication (SP) 800-171, Protecting Controlled Unclassified Information in Nonfederal Information Systems and Organizations, which currently includes 14 families of security requirements and a total of 110 individual controls.
The CUI requirements within NIST SP 800-171 are directly related to the baseline controls described in NIST SP 800-53, Security and Privacy Controls for Federal Information Systems and Organizations, and are intended for use by federal agencies in contracts or other agreements established between those agencies and non-federal organizations.
TestPros provides a full range of NIST Compliance Consulting Services to help you establish the necessary controls, and build the documentation the Government requires.
Do I need to be NIST 800-171 compliant?
If your business is contracted to provide services, goods or research funds to the U.S. federal government, then NIST SP 800-171 compliance becomes a critical responsibility for protecting controlled unclassified information. This includes contractors and service providers, organizations receiving funding from the state or federal government – as well as businesses supplying goods or services to any of these entities.

When will NIST 800-171 compliance be required?
Contractors providing services to the U.S. federal government are responsible for protecting CUI. For Department of Defense contractors, DFARS 252.204-7012 & 252.204-7008 require that you implement the safeguards defined by NIST SP 800-171 over these materials by December 31, 2017. Prior to the deadline, DoD contractors must report any NIST SP 800-171 requirements not implemented, within 30 days of contract award.
While no equivalent FAR regulations are currently in place that map to the DFAR requirements, there are Executive Orders that mandate compliance for all government agencies.
CUI requirements are based on Executive Order (EO) 13556 of November 4, 2010 as well as 32 CFR Part 2002, Controlled Unclassified Information (CUI) in effect November 14, 2017, and supported by “CUI Notice 2016-01: Implementation Guidance for the CUI Program,” which was issued by NARA September 14, 2016 (“Day-0”).
Per that guidance, agencies must be at an Initial Operating Capability (IOC) one year after Day-0 to be compliant, and be at Full Operating Capability (FOC) three years after Day-0 (September 14, 2019) to be compliant. It is only a matter of time before non-DoD agencies pass along the same CUI handling requirements to their contractors.
Regardless of the legal or statutory requirement, it makes good business sense to implement the security steps defined by NIST SP 800-171!
What are the control families in NIST 800-171?
This security family ensures that only authorized users can access sensitive data and system resources, implementing measures like role-based access control and multi-factor authentication to prevent unauthorized access.
This family focuses on providing employees with the necessary knowledge and understanding of security procedures, network maintenance procedures, and system security alerts to maintain a secure environment and protect sensitive data.
This security family generates audit trail evidence and maintains detailed records of system activities, helping organizations identify and investigate potential security incidents or unauthorized software installations.
This family includes establishing secure baselines and managing hardware, software, and network configurations to maintain a consistent and secure environment.
This family ensures that users and devices are properly identified and authenticated before being granted access to sensitive information and resources, reducing the risk of unauthorized access.
This security family focuses on preparing for, detecting, responding to, and recovering from security incidents, including creating a comprehensive incident response plan and training staff to follow established protocols.
This family encompasses regular maintenance activities, such as patching software vulnerabilities, updating security tools, and performing network maintenance procedures to keep systems secure and up-to-date.
This family involves the protection of sensitive data stored on physical media, such as hard drives or USB drives, through encryption, secure storage, and controlled access.
This family addresses the need for background checks, security training, and ongoing monitoring of employees with access to sensitive data to minimize insider threats and unauthorized access.
This family includes measures to secure physical facilities, such as access controls, surveillance systems, and environmental controls, to protect sensitive data and system resources from physical threats.
This family involves the identification, evaluation, and mitigation of potential risks to sensitive data and system security, helping organizations prioritize and implement appropriate security measures.
This family includes conducting regular security controls and procedures assessments to ensure their effectiveness and compliance with NIST 800-171 requirements.
This family focuses on securing communication channels and networks to prevent unauthorized access, data leaks, and potential cyberattacks, including the use of encryption, firewalls, and intrusion detection systems.
This security family ensures the accuracy, integrity, and availability of sensitive data and system resources by detecting and addressing potential vulnerabilities, unauthorized changes, and other security threats.
Steps to Conduct a NIST 800-171 Basic Assessment
Conducting a NIST 800-171 Basic Assessment involves a systematic approach to ensure your organization’s compliance with the required security practices. Here are the key steps to guide you through the process:
Certified &
Independent
Our Approach to Compliance
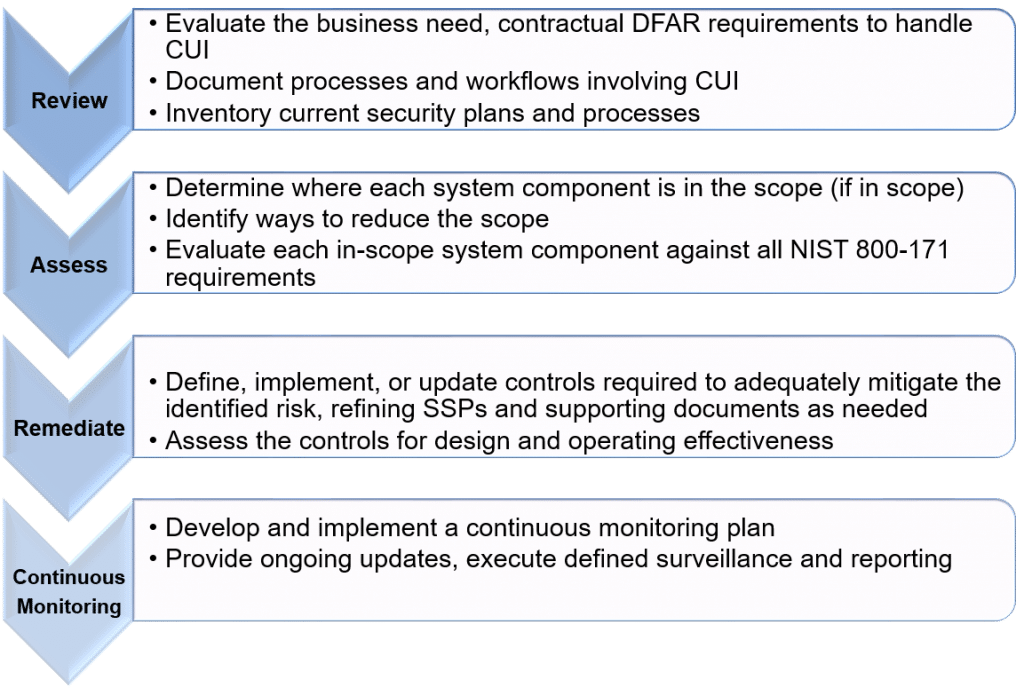
As illustrated in the figure, our Assessment Services include audits and compliance assessments against the NIST 800-171 standard, after which we advise on security program enhancements and control implementation where gaps are identified.
Our approach is pragmatic – where possible, we identify ways to reduce the scope of our client’s effort. For example, in lieu of hardening client-hosted servers and networks, it is often more expeditious and cost effective to isolate CUI data on FedRAMP-certified, cloud-based servers.
Client Deliverables
For each of the NIST 800-171 control objectives, TestPros delivers the following audit / assessment services and documentation:
- Identify applicable compliance guidance
- Determine if Group Policies (Active Directory or other LDAP), other Policies and Standards, Documented Processes and SOPs are in place
- Identify related technology considerations
- Document compliance status
- Justify any deviation from standard (pre-implementation only)
- Note any clarifying information, for example, reference to duplicate controls
Trusted Clients






System Security Plans (SSP) & NIST Remediation
Once we have helped our client identify their requirements, TestPros is available to help you create NIST 800-171 required documentation sets, including a System Security Plan (SSP) that documents how you protect and ensure control of CUI and any additional guidance based on client or agency requirements.
We develop supporting compliance programs, including cost-effective alternative approaches, to implement and maintain (continuous monitoring) the required controls for transmitting or storing this data in non-federal information systems. We work from either existing client or TestPros-provided templates to accelerate the process.

TestPros’ NIST 800-171 Consulting
Our experts understand that NIST 800-171 compliance begins with ensuring that Software, Hardware, and Document security measures are integrated into each IT requirement. This should be prioritized at the outset of the system development life cycle.
TestPros offers NIST 800-171 gap analysis, compliance support, program support, and training services to assist your organization safeguard it’s networks and become compliant!
Learn more about our services by clicking above or contact us here.
FAQ
What does it mean to be NIST 800-171 compliant?
To ensure the security of a company’s computer systems and data in compliance with National Institute of Standards and Technology (NIST) regulations, NIST 800-171 dictates that specific safeguards such as intrusion detection systems and firewalls must be applied. This is to protect against potential unauthorized access, use, disclosure, alteration or misappropriation of private information. If you’re unsure where your organization stands, give us a ring today.
How much does NIST certification cost?
NIST compliance costs can range from $5,000 to $100,000 depending on the size and complexity of the business. To save costs, many companies opt to outsource their compliance needs to a third-party or consultant. The cost of NIST 800-171 certification also follows the same trend; for smaller organizations with simpler systems it would be between $2,500 and $20,000 while larger enterprises with more complex systems might reach up to $50,000 or above.
What is Cybersecurity Maturity Model Certification (CMMC)?
The Cybersecurity Maturity Model Certification (CMMC) is a new framework that will replace the NIST 800-171 requirements in DFARS 7012 compliance. With a 3-tiered approach, CMMC accounts for an organization’s current cybersecurity posture. It also outlines the specific steps needed to improve it. The focus is to reduce risk in DoD supply chains.
Read our post that outlines specific steps for CMMC Compliance.
Where do you offer your services?
Our headquarters are in Sterling, VA, however we offer NIST consulting globally and across the USA, including cities such as Washington D.C., and St. Louis, MO.
What is the recommended log retention period?
To comply with NIST 800-171 requirements, the National Institute of Standards and Technology (NIST) suggests that organizations should maintain system event logs for no less than 180 days—extending this period depending on any legal or business considerations. Furthermore, it is imperative to guarantee sufficient storage resources as well as encrypt all stored log data to shield against unauthorized access.
How often should you perform a vulnerability scan?
To stay compliant with NIST 800-171, organizations must regularly perform vulnerability scans via automated tools. These scannings discover any existing weaknesses or possible vulnerabilities in your system or application and should be closely reviewed to detect areas of concern. Necessary corrective measures are then taken – if needed – to remain adherent to the standards set by this security measure.
What Challenges
Are You Facing?





